
A new threat is creeping through the Linux world, and it’s using a surprising disguise. Researchers at Aqua Nautilus have uncovered a malware strain known as Koske. This one isn’t just some recycled script. It shows signs of being assisted by artificial intelligence, possibly written with help from a language model. That’s a scary thought on its own, but it gets worse.
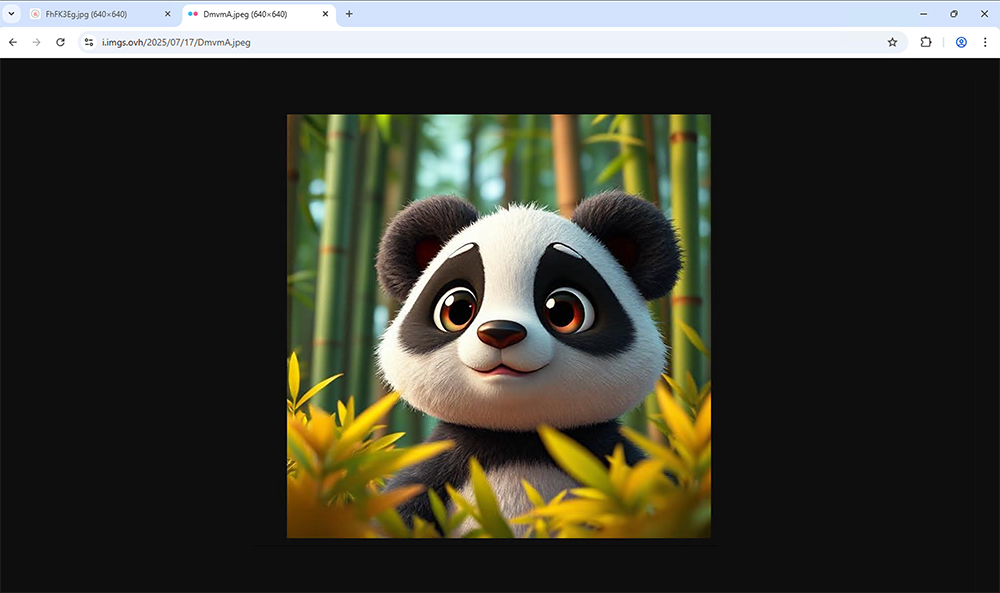
The malware is hidden inside what looks like an ordinary image of a panda bear. Yes, seriously. The photo looks completely normal. But buried at the end of the file is a payload designed to infect and take control of Linux systems. This trick is called polyglot file abuse. It’s different from steganography, where data is tucked into pixels. Instead, the payload is just stuck at the end of a working JPEG file. Open it in a photo viewer, and you’ll see a cute bear. Open it with a script, and you’ll trigger a hidden attack.
The campaign starts when attackers find misconfigured JupyterLab servers. From there, they connect using a Serbian IP address and download a pair of image files. These files contain shell scripts and raw C code, which get extracted and run directly in memory. That approach helps the attack fly under the radar of most antivirus tools.
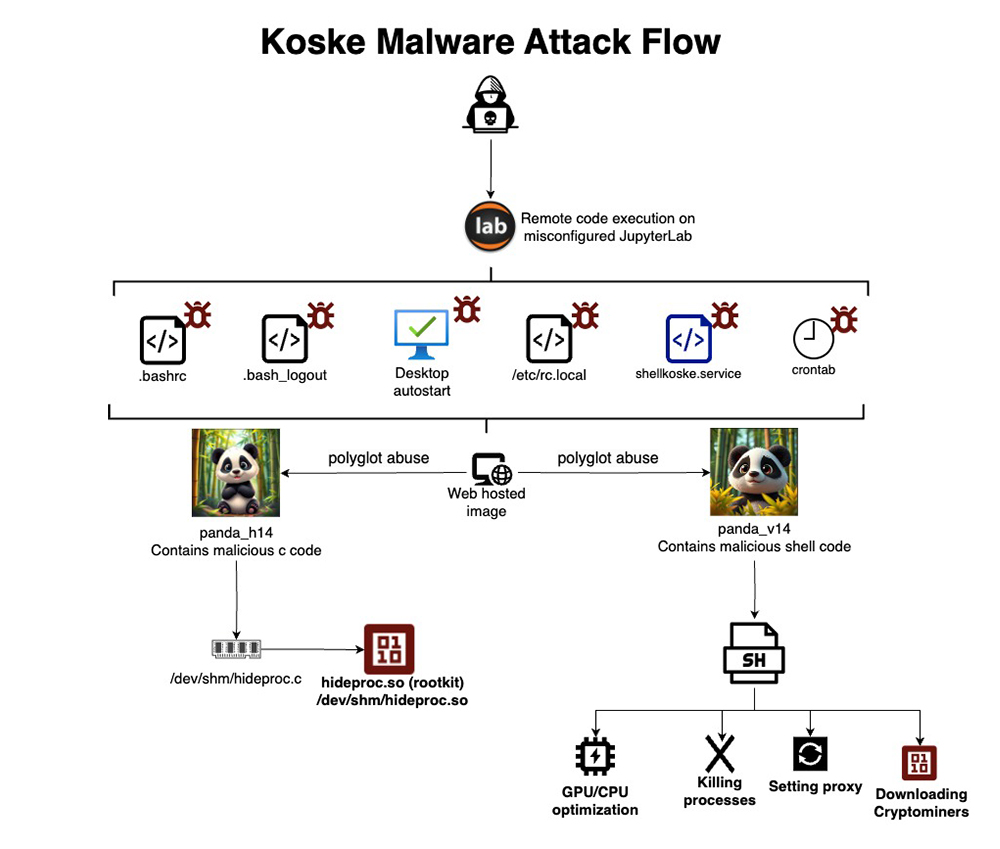
Once inside, Koske works hard to stick around. It edits the .bashrc and .bash_logout files to execute a hidden script at every login. It also modifies /etc/rc.local and installs a new systemd service called shellkoske.service. On top of that, it sets up scheduled cron jobs to keep itself running no matter what.
One of the payloads delivers a userland rootkit. This piece of C code gets compiled on the fly and hijacks the readdir() function using LD_PRELOAD. That makes it capable of hiding processes, files, and directories from tools like ps and top. Anything labeled with names like koske, hideproc, or hideproc.so simply vanishes from view. The malware stores its hidden process ID in a file under /dev/shm, which makes things even harder to detect.
The rootkit and scripts don’t come from random forums or shady servers. They’re pulled from free image hosting platforms and GitHub. One of the GitHub accounts, named vozstanica, appears to exist only to serve cryptomining binaries. Koske supports at least 18 different cryptocurrencies, including Monero, Ravencoin, and Zano. It evaluates the infected system’s hardware and selects a miner optimized for either CPU or GPU. If a mining pool goes offline or fails, it automatically switches to a different one.
Koske is built to survive in nearly any environment. It resets proxy settings, flushes iptables rules, and overwrites the system’s DNS configuration with Cloudflare and Google servers. Then it locks those changes using chattr +i, which makes them tough to undo.
Where things start feeling more futuristic is in how the malware adapts. It includes a diagnostic module that checks connectivity using tools like curl, wget, and direct TCP connections. If any of those fail, it triggers a fix. It also pulls fresh proxy lists from GitHub and tests different protocols like SOCKS5 and HTTP until it finds one that works. This isn’t just malware that runs a script and disappears. It diagnoses problems, solves them, and keeps going.
Even the structure of the code is suspiciously clean. It’s well-commented, defensive in its scripting habits, and modular in ways that feel like they came from an AI helper. Some of the text includes Serbian phrases, probably to confuse attribution efforts. This kind of polish is rare in average malware.
The implications are huge. Koske could be just the start of a new wave of threats written, refined, or completely generated by AI. That means defenders can no longer assume that malware will be sloppy or poorly structured. In fact, AI may already be making attackers faster and better than ever before.
If you run Linux in any serious capacity, it’s time to take runtime security more seriously. Watch for unusual modifications to .bashrc, keep an eye on DNS settings, and review your list of systemd services often. Just because you don’t see a miner running doesn’t mean it isn’t there.
Koske blends clever persistence with strong evasion and likely AI-generated logic. That combination is a major warning sign. Future malware could go even further, possibly reacting to defenses in real time or rewriting itself to avoid detection entirely.
Welcome to the era of AI-shaped threats. The panda is just the beginning.


